Ransomware has evolved from random attacks into a targeted business. In 2025, Asia-Pacific (APAC) has become one of the most active regions for ransomware groups, from Singapore’s finance hubs to manufacturing plants in Vietnam, Malaysia, Thailand and many more. Attackers aren’t just after money; they’re after data, disruption, and leverage.
Why APAC is a Prime Target?
APAC’s fast digital growth has outpaced its security maturity. Many small and midsized businesses have moved data to the cloud without proper protection, and critical industries like manufacturing and logistics still rely on older systems that can’t easily be patched.
In the meantime, ransomware attacks have also developed itself to be more sophisticated and direct than ever. There are reports that recent attacks have been incorporated with generative Artificial Intelligence (GenAI) and large language models (LLMs), giving cybercriminals smarter tools to deceive victims and outpace defences. Imagine ransomware that rewrites itself every few hours, or phishing messages that perfectly imitate your CEO’s tone. That’s the reality which security teams across APAC are facing in 2025.
APAC Countries are now being heavily targeted
The Evolution of Ransomware Tactics.
Ransomware has come a long way from simply locking files and demanding payment. Today, attackers use multiple layers of pressure to ensure victims pay and what started as “double extortion” has now evolved into quadruple extortion.
In the past, attackers would not only encrypt a company’s data but also steal it and threaten to publish it online, which was double extortion. By 2025, many ransomware groups have added two more steps:
- Third extortion: directly contacting the victim’s customers or partners, alerting them that their data may be exposed unless payment is made.
- Fourth extortion: launching distributed denial-of-service (DDoS) attacks or public smear campaigns to damage the victim’s reputation and force a faster response.
Example:
A logistics company in Australia recently faced a quadruple extortion attack. The attackers encrypted servers, stole shipment records, emailed major clients about the breach, and flooded the company’s website with traffic to take it offline. The campaign was linked to the BlackCat/ALPHV ransomware group, who are known for using every available pressure point to force compliance.
This new playbook shows how ransomware has become a full-scale coercion strategy, not just a technical attack. Each layer adds financial, legal, and reputational pain, making proactive defence and clear response plans more critical than ever.
Supply Chain Attacks are growing.
Instead of attacking one company at a time, ransomware operators now target vendors and service providers that connect to many clients. Compromising one trusted platform can lead to dozens of victims.
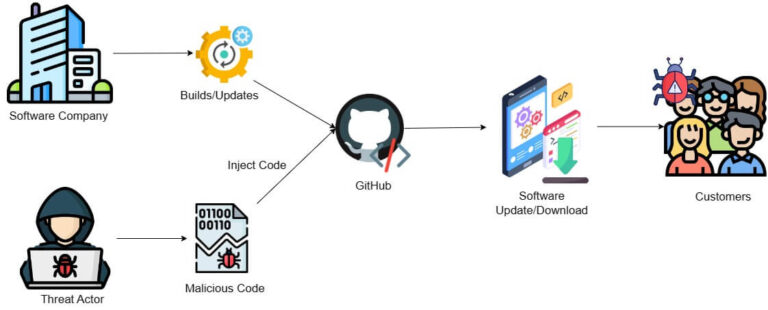
How a Supply Chain Attack works
Example:
A Singapore-based IT firm providing remote monitoring tools was compromised through a vulnerable plugin. The attackers then spread ransomware to multiple downstream customers, from law firms to logistics providers overnight. The incident demonstrated how third-party dependencies can quickly multiply risk.
Even well-protected companies can fall victim if their vendors aren’t equally secure.
Manufacturing & Logistics under fire.
Factories, ports, and logistics networks are prime targets because downtime directly affects business operations. Attackers know that every hour offline costs thousands — and that urgency increases the likelihood of payment.
Example:
A Japanese automotive parts manufacturer was hit by the Cl0p ransomware group in early 2025, halting production for several days. The entry point was traced to a misconfigured VPN account with no multi-factor authentication. The ransom demand — roughly US$3 million — was small compared to the operational losses incurred during the shutdown.
The New Ransomware Economy
Ransomware is no longer a single operation, but it’s an ecosystem. Groups like LockBit, BlackCat, and Cl0p operate on a “ransomware-as-a-service” model, renting their tools to affiliates in exchange for a share of profits. These affiliates handle the actual attacks, making the ecosystem harder to dismantle.
Some groups now use Generative AI (GenAI) and large language models (LLMs) to scale their operations, writing phishing emails, translating ransom notes into local languages, and automating negotiation chats with victims. The result: faster, more convincing, and more persistent attacks across APAC.

AI can also contribute to the defensive side as well
How can APAC Businesses respond?
No single tool can stop ransomware entirely. But layered, disciplined preparation can turn a potential crisis into a contained incident. Here’s how organisations across the Asia-Pacific region can strengthen their resilience:
- Segment and back up critical data
Separate your most valuable systems, such as finance, HR, and production from less critical networks. This limits how far ransomware can spread if one system is compromised. Backups should be offline, immutable, and regularly tested for restoration. In a Singapore manufacturing case, the company avoided a multimillion-dollar ransom because its backups were stored on isolated servers disconnected from the main network. - Mandate phishing-resistant MFA
Many breaches still begin with stolen or reused credentials. Implement phishing-resistant multi-factor authentication (like passkeys or FIDO2 security keys) across all remote access points, VPNs, and admin accounts. These make credentials useless, even if an employee falls for a phishing email. - Test your incident response plan
A plan only works if it’s practiced. Run tabletop exercises simulating ransomware and data leak scenarios, involving both IT and business leaders. Define who communicates with regulators, media, and customers. Companies that have rehearsed these steps tend to restore operations faster and avoid costly panic decisions during real attacks. - Assess third-party and supply-chain risk
Your cybersecurity is only as strong as your weakest partner. Require vendors and IT service providers to meet minimum security baselines, like MFA, regular patching, and encryption standards. When possible, review their SOC 2 or ISO27001 certifications. After several 2024 APAC ransomware incidents spread through managed service providers, many firms now include security clauses in vendor contracts to enforce accountability. - Invest in regional threat intelligence
Attack patterns vary across countries. For instance, LockBit and Cl0p have shown a strong focus on manufacturing and logistics sectors in Southeast Asia, while BlackCat has targeted finance and IT services in Australia and Japan. Subscribing to regional threat intelligence feeds or partnering with cybersecurity vendors who track local trends can help you identify early indicators of compromise before the damage is done. - Focus on people, not just tools
Technology matters, but employee awareness remains the first line of defence. Regular, short phishing simulations and cyber hygiene workshops can dramatically reduce risky clicks. Encourage a culture where staff feel safe to report suspicious emails or incidents immediately.
Final Thought
Ransomware has grown into a calculated, multi-layered threat that blends technology, psychology, and public pressure. The APAC region’s interconnected supply chains and digital-first economies make it especially vulnerable, but not helpless.
Preparation, visibility, and discipline are the strongest defences. In a world where attackers use every tactic available, the best time to prepare is before they knock on your door.
